ACI Fallback Login Domain
In Productive ACI Fabrics, you have the flexibility to use a range of external authentication mechanisms, such as RADIUS, LDAP, RSA, TACACS+, etc., for user authentication and authorization. This variety allows you to choose the method that best suits your needs.
But to have a backup option, in case of failure of the external authentication system, you want to have an alternative to be still able to log in to your ACI Fabric.
For this purpose, it is essential to configure a dedicated Fallback Domain or use the built-in fallback domain. This ensures continuous access to your ACI Fabric and provides a safety net for accessing the ACI Fabric as an administrator in case of an emergency.
ACI configuration to enable the fallback login domain
The configuration for enabling fallback login features varies by ACI version. We will outline this for the current releases.
There are two primary methods to configure the fallback domain: you can either allow it to be used at all times or only when the main Login Domain is unavailable.
ACI Version 5.3 and earlier
Under Admin -> AAA -> Authentication you find the main Dashboard where you can configure the fallback domain.
There exists a dropdown “Fallback Domain Availability” where you can choose between two options Always Available Available only if no providers are reachable via ICMP

I highly recommend using the “Always Available” option because otherwise, you could be stuck in a State where the providers are reachable via ICMP but may not function otherwise. Then, you would be unable to log in to the ACI Fabric with the fallback user.
ACI Version 6.0 and later
Under Admin -> AAA -> Authentication you find the main Dashboard where you can configure the fallback domain.
You have to click on the pencil icon to edit the configuration.
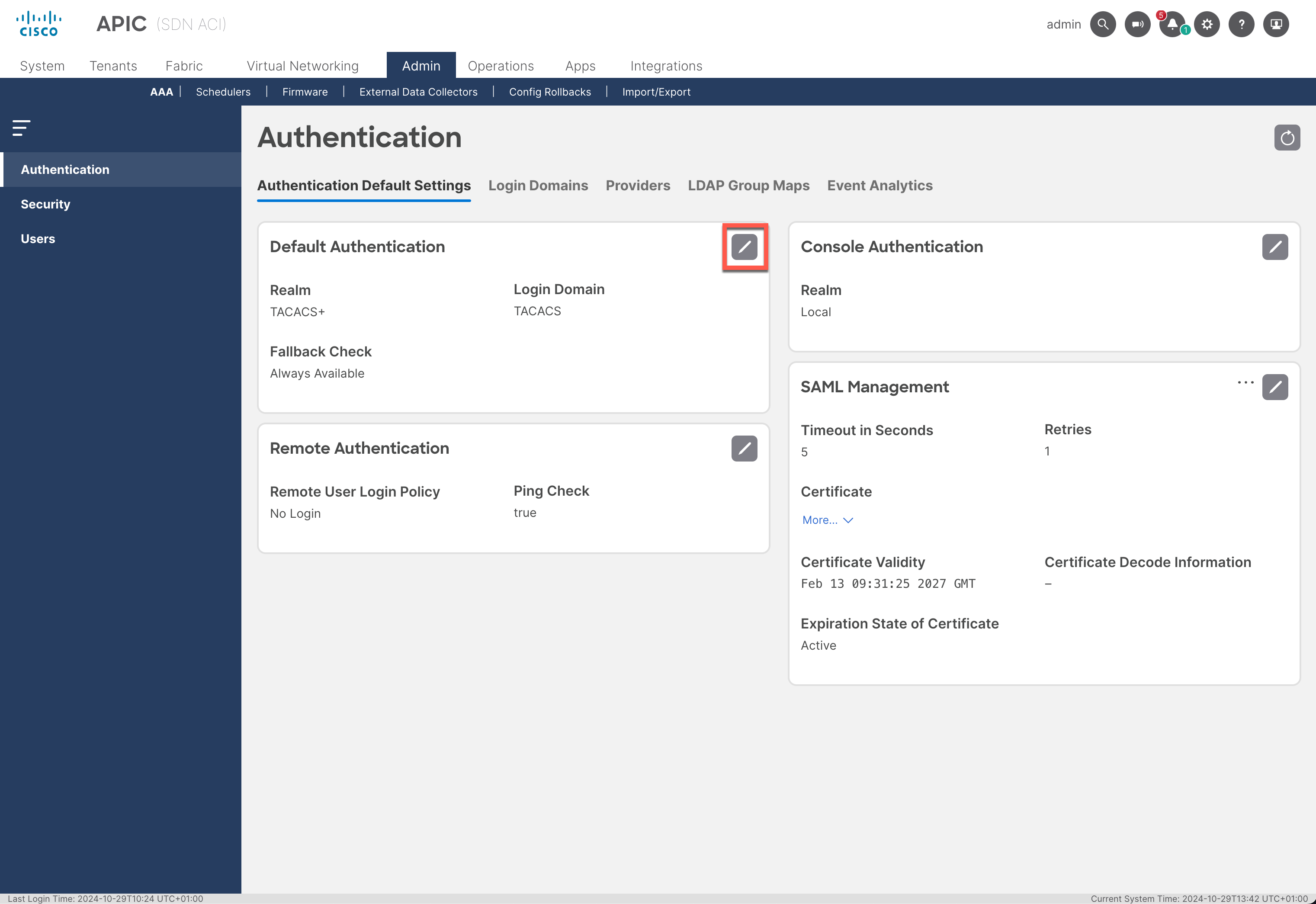
The naming is unlucky. “Enabled” is refered to “Disables fallback if default authentication has active servers”

So if you select the “Enabled” option, you can only use the fallback when the authentication servers are unreachable. There is also a Warning “Warning: Fallback domain will be unavailable if (for some reason) the AAA server is pingable but unable to authenticate users (due to connectivity issues).”
I strongly advise against enabling this setting. Not enabling the setting allows you to log in to the fabric with the fallback user, even when the primary authentication servers are accessible.
How to use the fallback login domain
GUI
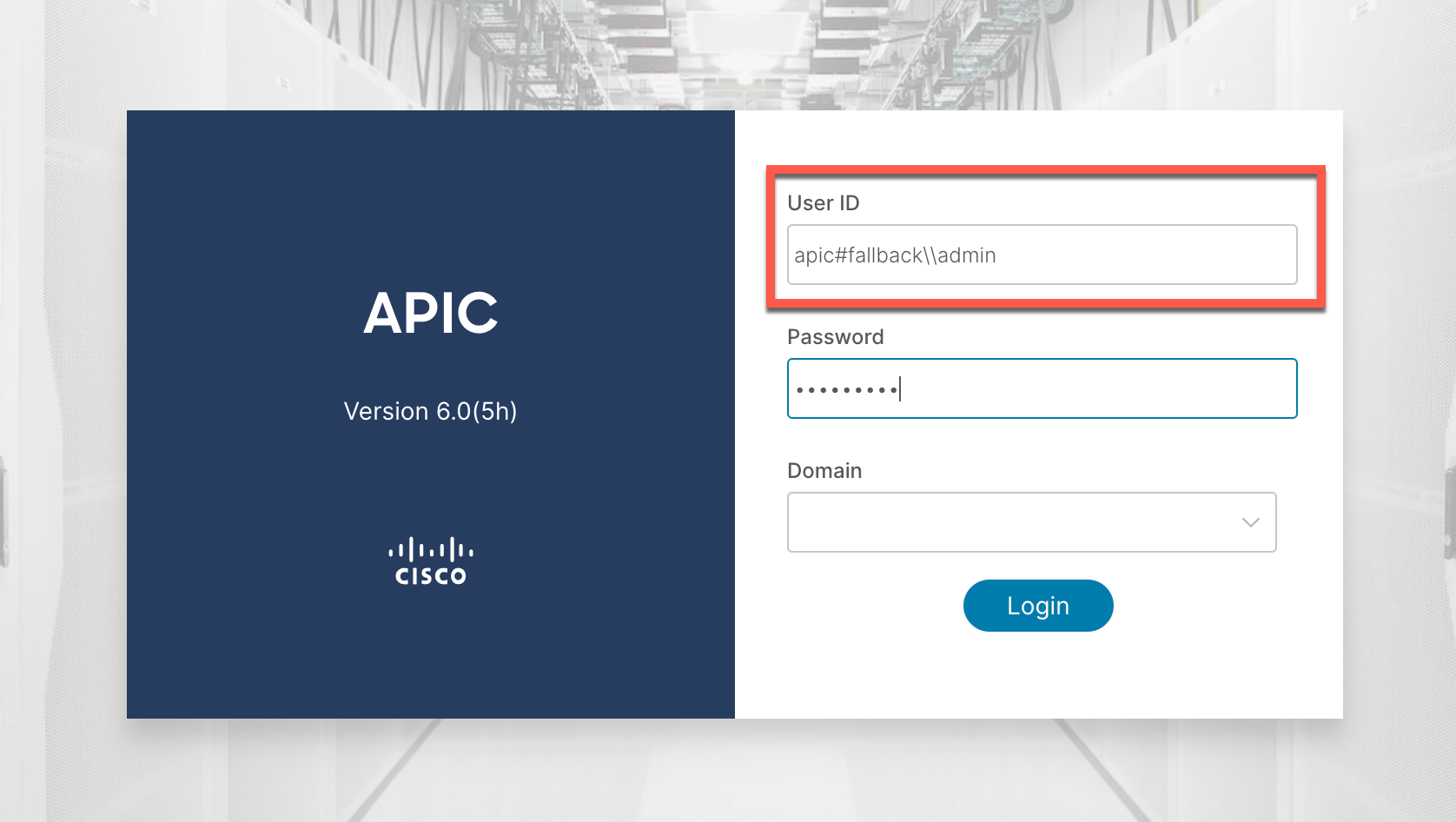
In the GUI, you can use the fallback by providing the user “apic#fallback\admin” with the corresponding password.
SSH/CLI
To use the fallback domain with the CLI, you specify the user similarly.
|
|